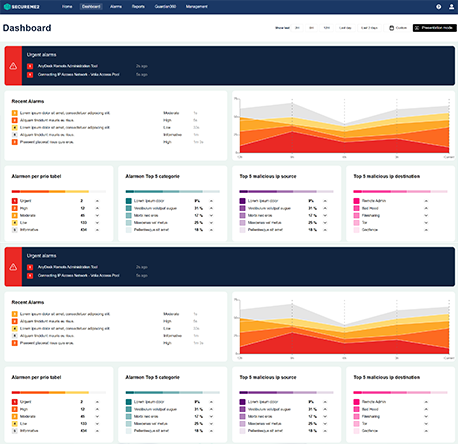
“Cyberalarm Pro from SecureMe2, enables us to guarantee the continuity of our production lines. Thanks to the real-time insights they provide, we can immediately deal with malicious behaviour or misuse of systems.”
CFO – Harvill Food Group BV“This is great, I have been able to ban many threats from my network with Cyberalarm so far. Just great! We are able to monitor everything that is happening in our online space, while without Cyberalarm you easily miss something. Forget it, check it.”
System Administrator – Alfa Bier“As far as I’m concerned, two rules apply in the world of technical cyber resilience: 1) there are no rules and 2) without insight there is no overview. We have deployed Cyberalarm as one of the first steps within the Managed Detection and Response Service that we set up. From the role of ‘independent watchdog’ and as a supplier of current Cyber Threat Intelligence data, our MDR is fed 24/7 with the analysis of (potentially) malicious behavior. Cyberalarm gives us the necessary insight into our own network traffic.”
IT-specialist – municipality of Enschede